![]()
Concept
The keys to functional verification are “verification strategy” and “highly complete verification item extraction.”
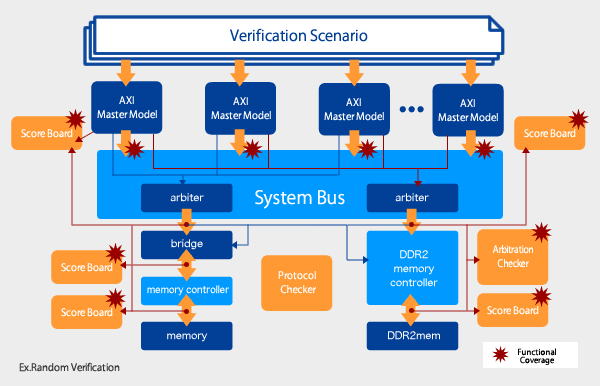
Our functional verification services emphasize highly complete verification item extraction while also generating test benches and functional scenarios, random verification, and even functional coverage to meet customer demands by providing these services from a wide variety of angles. By implementing functional verification on the RTL and C models designed by customers from a third-party perspective, we improve quality of customers’ circuits.
Verification Item Extraction Services
In our verification item extraction services, we propose the optimal verification strategy for our customers while also providing verification item extraction services using the methodology in the IP Functional Verification Guide developed by STARC (Semiconductor Technology Academic Research Center). We use our customer’s functional specification as the interface.
Random Verification Services
We perform random verification and coverage-driven verification that make full use of cutting-edge verification methodologies. Our verification methodologies apply to OVM, VMM, and UVM. We implement random verification in an optimal verification environment to our customers’ design environment and design tools.
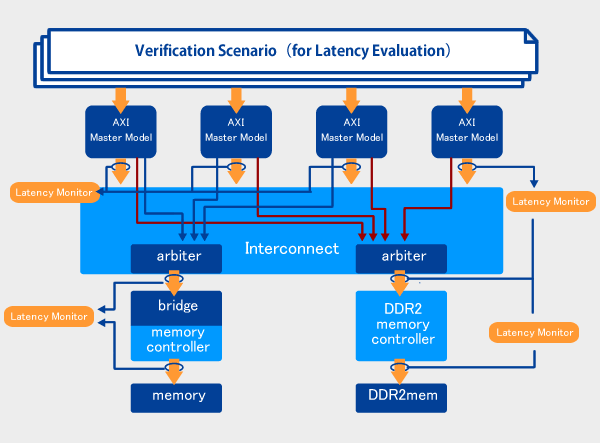
System Verification Services
While verifying the operation of the SoC systems designed by our customers with use case, we carry out functional verification of these systems.
By collecting necessary information, such as the number of transactions and the latency with the functional monitor, we understand the bottlenecks, such as the memory transfer concentration on ahead, then feed it back to the demand specifications and functional specifications.
We optimize the operations as our customers’ own systems.